Want to make browsing safer for everyone on your network? DNS filtering might be the answer. It enforces SafeSearch, blocks harmful content, and ensures compliance with security policies – all without needing individual device setups. Here’s what you need to know:
- What is DNS Filtering? It controls DNS queries to block harmful sites and enforce SafeSearch (e.g., Google, YouTube, Bing).
- Why Use DNS for SafeSearch? It provides network-wide protection, scales easily, enhances productivity, and meets regulations like CIPA and HIPAA.
- How to Set It Up: Use resolvers like CleanBrowsing to redirect queries to SafeSearch servers and block inappropriate content.
DNS filtering ensures a safer, faster, and more productive online experience for schools, businesses, and families. Ready to set it up? Keep reading for step-by-step guidance.
🛡️ CleanBrowsing: Internet Safety Made Simple
Filter harmful websites, block adult content, and protect your entire network. All with fast, privacy-respecting DNS.
Start Filtering Here →How to Configure DNS Filtering for SafeSearch
To enforce SafeSearch across your network, redirect DNS queries by configuring your settings to use CleanBrowsing’s DNS servers. This setup ensures SafeSearch is automatically applied to all devices connected to your network.
Steps to Enable SafeSearch via DNS
Start by updating your network settings to use CleanBrowsing’s DNS IPv4 addresses. CleanBrowsing offers predefined filtering profiles that handle search queries automatically. For example, the Family Free DNS Filter profile redirects:
- Google to
forcesafesearch.google.com - YouTube to
restrictmoderate.youtube.com - Bing to
strict.bing.com
CleanBrowsing also supports encrypted DNS protocols like DoH (DNS over HTTPS), DoT (DNS over TLS), and DNSCrypt, which help prevent users from bypassing the filter. Additionally, administrators have the option to customize their filtering setup by creating specific allow and block lists, complementing the SafeSearch enforcement.
Once configured, DNS updates typically take just a few minutes to apply, ensuring SafeSearch is active on all connected devices. After completing the setup, it’s essential to verify that SafeSearch is functioning as intended.
How to Verify SafeSearch Configuration
You can confirm SafeSearch is active through visual checks or by using command-line tools.
- Visual Verification:
- On Google, check for the “SafeSearch on” message at the top right of the search results page. Attempts to disable SafeSearch should have no effect.
- For YouTube, Restricted Mode should appear enabled at the bottom of the results page, often accompanied by a note that the setting is managed by the network administrator.
- On Bing, the SafeSearch setting should display as “Strict.” Clicking on it should lead to an informational page without allowing changes.
- Command-Line Verification:
Using thenslookupcommand, administrators can confirm DNS redirection. Here’s what you should see for each search engine:
| Search Engine | Expected nslookup Result | Notes |
|---|---|---|
nslookup www.google.com → forcesafesearch.google.com → 216.239.38.120 | Google SafeSearch enforcement via CNAME | |
| YouTube | nslookup www.youtube.com → restrict.youtube.com or restrictmoderate.youtube.com → 216.239.38.120 and 2001:4860:4802:32::78 | YouTube has two levels: restrictmoderate (moderate) and restrict (strict) |
| Bing | nslookup www.bing.com → CNAME pointing to strict.bing.com or containing “strict” | Enforces Bing SafeSearch in strict mode |
Make sure to perform these tests on devices connected to the filtered network.
Regular checks of your SafeSearch setup can help you spot issues like DNS caching errors, incorrect configurations, or bypass attempts. This ensures your network stays secure and maintains a family-friendly environment.
DNS Filtering Policy Best Practices
Setting up effective DNS filtering policies requires a structured and thoughtful approach to ensure SafeSearch is consistently enforced. DNS policies operate on a top-down evaluation system, meaning the order of your policies determines how they apply across user groups and devices. Start by establishing a restrictive default policy as the baseline. This default should enforce SafeSearch across all major search engines. From there, create exceptions in order of specificity – beginning with broader rules and narrowing down to more specific ones. For instance, you could enforce a strict policy for all users, a slightly relaxed policy for administrative staff, and specific allowances for IT personnel who need broader access for troubleshooting.
Additionally, when you assign new users or devices to top-level groups, they automatically inherit the associated DNS policies. To prevent conflicts, prioritize specific policies over broader ones. If managing mobile or roaming users, consider location-based adjustments to maintain SafeSearch enforcement, no matter the network type. This structured framework helps ensure seamless monitoring and smooth handling of encrypted traffic.
Policy Hierarchy and Priority
The top-down evaluation system means DNS policies are applied in the order they appear, making their arrangement critical. A good starting point is a restrictive default policy that enforces SafeSearch for all major search engines. Afterward, introduce exception policies, moving from general to specific. For example:
- A restrictive policy for all users
- A slightly more lenient policy for administrative staff
- Specific allowances for IT personnel needing broader access
New users or devices inherit policies automatically when added to their respective groups. To avoid conflicts, ensure broader rules are assigned lower priority compared to more specific ones. For roaming or mobile users, location-based adjustments can help maintain SafeSearch enforcement, regardless of the network they connect to.
Monitoring and Updating Policies
Regular monitoring ensures your DNS filtering policies stay effective as search engines change and new threats arise. DNS logs are a treasure trove of insights, helping identify issues like repeated access to untrusted domains or unusual traffic patterns that might signal bypass attempts. To stay ahead:
- Review DNS logs weekly for suspicious activity. Consider integrating your logs into a SIEM (e.g., Trunc) for analysis and storage.
- Conduct monthly policy assessments to ensure settings are still relevant.
- Perform quarterly SafeSearch tests to verify enforcement and usability.
Stay informed about technical developments and adjust your policies as needed. Always document changes and evaluate their impact on network performance and user experience. With consistent monitoring and updates, you’ll be better equipped to handle challenges like encrypted DNS traffic.
Managing Encrypted DNS Traffic
Encrypted DNS protocols, such as DNS over HTTPS (DoH) and DNS over TLS (DoT), add privacy and security but also bring enforcement challenges. These protocols can make it harder to monitor or modify DNS traffic. Among the two, DoT is often preferred because it allows for easier monitoring and blocking of DNS queries.
However, certain browsers and applications can bypass DNS filtering. For example, Chrome introduced DoH support in May 2020, and Mozilla enabled DoH by default in Firefox back in 2019. To address this, administrators should configure endpoints to use DoH or DoT resolvers in strict mode through secure device management tools. This ensures encrypted DNS traffic is still filtered. Platforms like CleanBrowsing support both DoH and DoT, enabling SafeSearch enforcement while benefiting from encrypted DNS.
A hybrid approach can be effective: use transparent SafeSearch redirects for organization-issued devices, where you have full control, and rely on DNS-based SafeSearch for personal devices connecting to your network. Test compatibility with your cybersecurity tools to ensure that SafeSearch enforcement remains intact even with encrypted DNS.
Finally, remember that DNS filtering operates on an implicit allow principle – if a threat isn’t explicitly blocked, it will be allowed. This makes it essential to account for both known risks and potential bypass methods when designing your encrypted DNS strategy.
Using CleanBrowsing for SafeSearch Enforcement
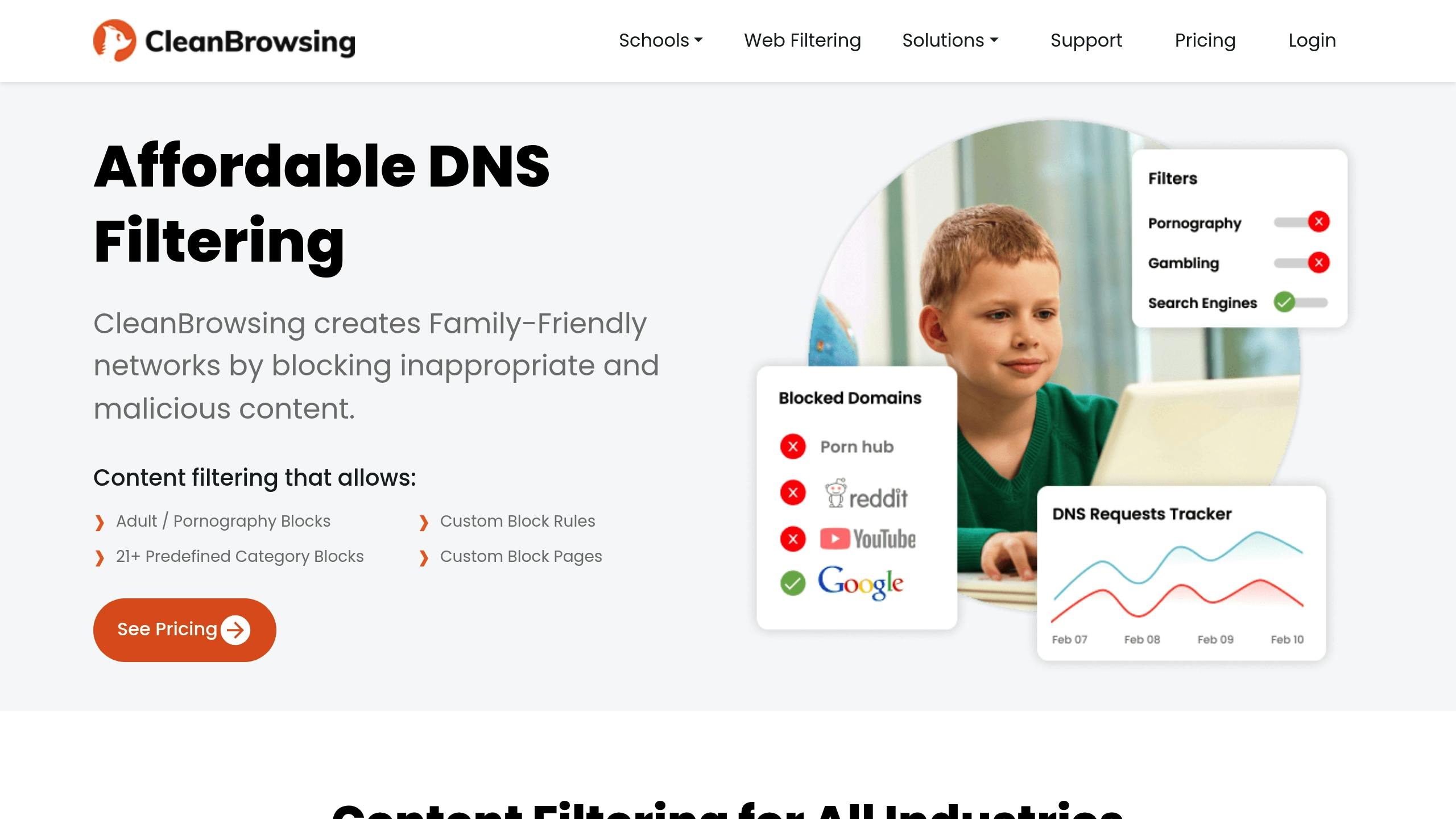
CleanBrowsing takes DNS filtering to the next level by integrating automated controls and a user-friendly dashboard, making SafeSearch enforcement both efficient and straightforward. While DNS filtering is essential for managing online access, CleanBrowsing simplifies the process by automating SafeSearch enforcement, reducing the need for manual configurations, and boosting overall network security.
CleanBrowsing SafeSearch Features
One of CleanBrowsing’s standout features is its automatic enforcement of Google Safe Search – no additional setup required. This functionality isn’t limited to Google; it extends to any search engine / platform that makes it publicly accessible, making it a reliable choice for organizations juggling multiple devices and users.
CleanBrowsing also ensures encrypted DNS connections through protocols like DoH, DoT, or DNSCrypt, keeping SafeSearch active and secure. The platform’s dashboard provides real-time monitoring, giving administrators insight into network activity and attempts to access blocked content.
🔍 Investigate DNS like a Pro with DNSArchive
Uncover historical DNS records, IP reputation data, and web metadata with one powerful tool. Built for threat hunters, researchers, and digital forensics teams.
Explore DNSArchive →📦 Push DNS Logs to a Secure SIEM with Trunc
Trunc helps you forward CleanBrowsing DNS logs—and other system logs—to a secure, cloud-hosted SIEM. Get real-time visibility, threat detection, and compliance reporting without the overhead.
Explore Trunc →🚀 Power Your Web Infrastructure with NOC
NOC combines authoritative DNS, a global CDN, and an intelligent WAF into one high-performance platform. Protect your sites, reduce latency, and gain full control over your delivery stack.
Visit NOC →DNS filtering simplifies SafeSearch enforcement across entire networks, removing the need for device-specific configurations. Unlike browser-based controls, which are often bypassed and require constant upkeep, DNS filtering operates at the network level, offering centralized and device-independent protection.
